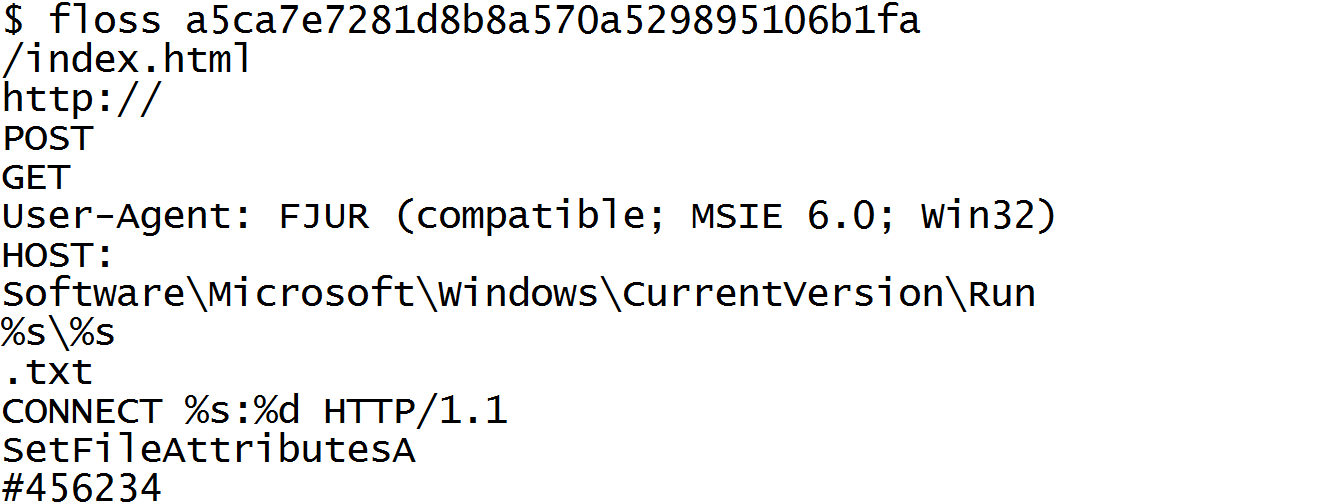
![Nick Carr on X: "The FireEye Labs Obfuscated String Solver (#FLOSS) shows a single stackstring: "80.85.157[.]238" - try it yourself: https://t.co/CrOHwCCM3e When run dynamically, the encoded SCT drops and executes this binary, Nick Carr on X: "The FireEye Labs Obfuscated String Solver (#FLOSS) shows a single stackstring: "80.85.157[.]238" - try it yourself: https://t.co/CrOHwCCM3e When run dynamically, the encoded SCT drops and executes this binary,](https://pbs.twimg.com/media/DWbb_oZVMAAaG_m?format=jpg&name=large)
Nick Carr on X: "The FireEye Labs Obfuscated String Solver (#FLOSS) shows a single stackstring: "80.85.157[.]238" - try it yourself: https://t.co/CrOHwCCM3e When run dynamically, the encoded SCT drops and executes this binary,

Evade Strings Detection with Stack Based – Cyber Security Architect | Red/Blue Teaming | Exploit/Malware Analysis

FLOSS Every Day: Automatically Extracting Obfuscated Strings from Malware- SANS DFIR Summit 2016 - YouTube

FLOSS - FireEye Labs Obfuscated String Solver (Automatically extract obfuscated strings from malware)
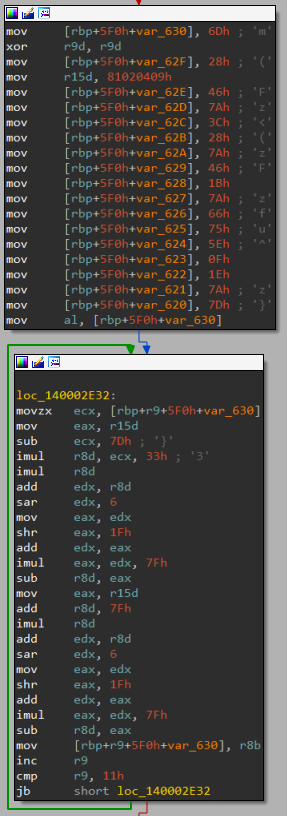
Automatically Extracting Obfuscated Strings from Malware using the FireEye Labs Obfuscated String Solver (FLOSS) | Mandiant
GitHub - mandiant/stringsifter: A machine learning tool that ranks strings based on their relevance for malware analysis.
Automatically Extracting Obfuscated Strings from Malware using the FireEye Labs Obfuscated String Solver (FLOSS) | Mandiant

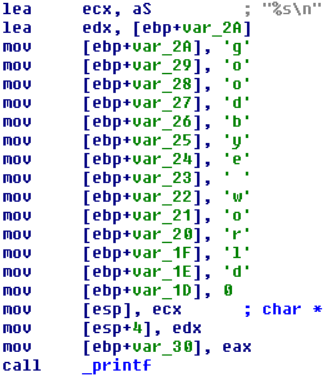
![Reverse Engineering Tips] — Strings Deobfuscation with FLOSS | by Thomas Roccia | SecurityBreak Reverse Engineering Tips] — Strings Deobfuscation with FLOSS | by Thomas Roccia | SecurityBreak](https://miro.medium.com/v2/resize:fit:663/1*gxMIULNbeSTuioMrJo934Q.png)


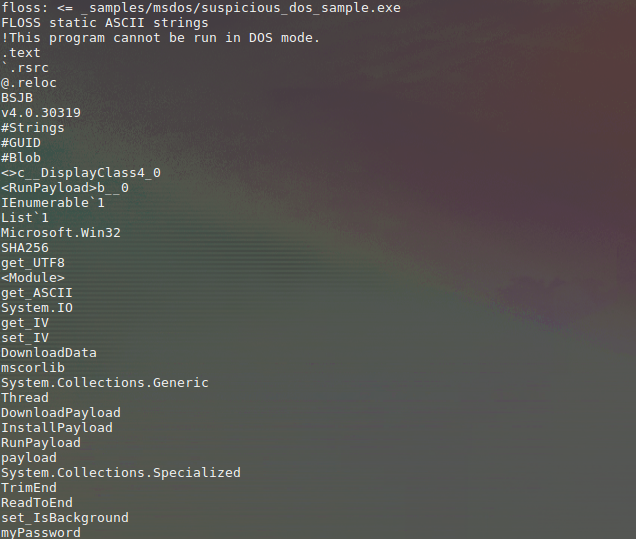
.png)
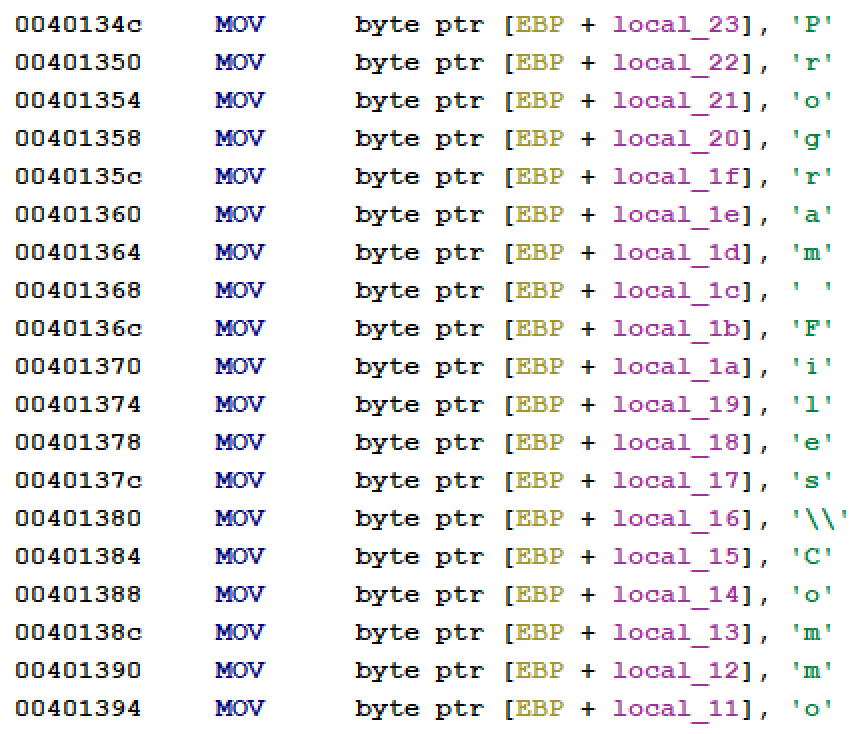

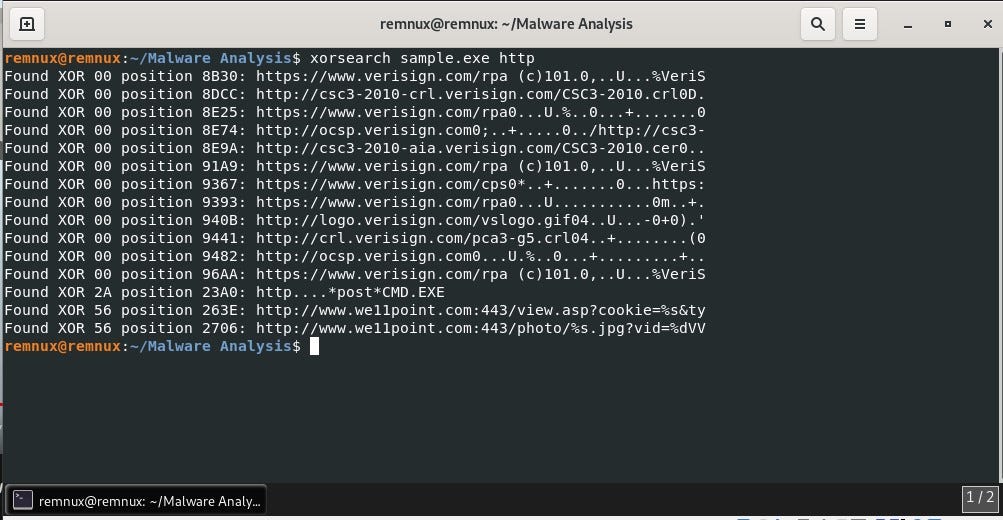

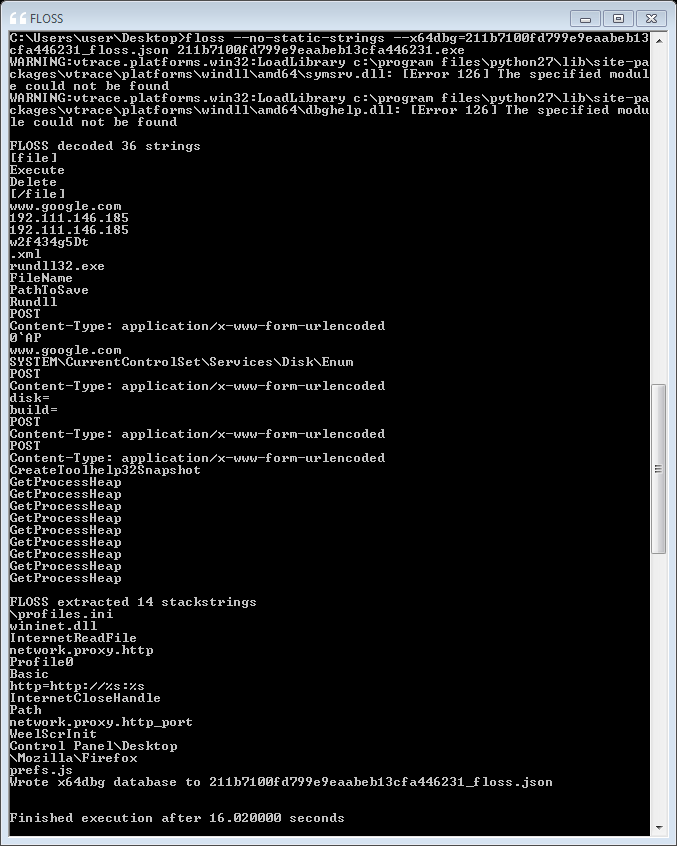
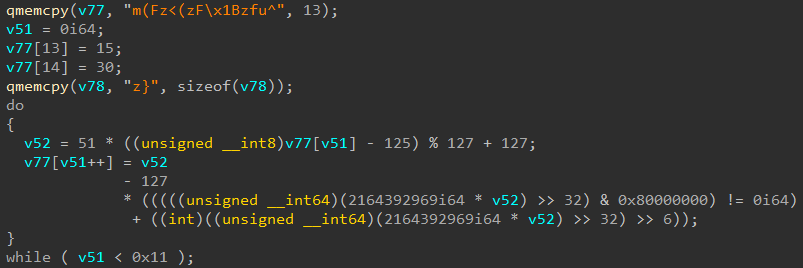

![Reverse Engineering Tips] — Strings Deobfuscation with FLOSS | by Thomas Roccia | SecurityBreak Reverse Engineering Tips] — Strings Deobfuscation with FLOSS | by Thomas Roccia | SecurityBreak](https://miro.medium.com/v2/resize:fit:1224/1*55MRyQ6lvtCPMQ5gBblIyg.png)